

Sustainable Development
Information Security
Today many things are done online, such as shopping, investing, and socializing. Information security is a part of the everyday life, and ensuring information security is essential to protection of customers’ rights and stability of financial markets.
Information Security Governance Strategy
TCFHC follows domestic and foreign regulations, guidelines and business requirements on information security, such as the “Financial Holding Company Act”, the “Guidelines for Cross Marketing among Subsidiaries of Financial Holding Company”, and the “Personal Data Protection Act”, to implement information security management policies, install management systems and create task forces in order to enforce information security in the Group. TCFHC has the “Guidelines for Responding to Computer Information Security Emergencies” and an interdepartmental “Information Security Response Team” in place as well as a reporting system. Regular drills are organized to ensure employees are able to respond and to effectively reduce the impacts of information security incidents. TCFHC also refines the protective measures on an ongoing basis.
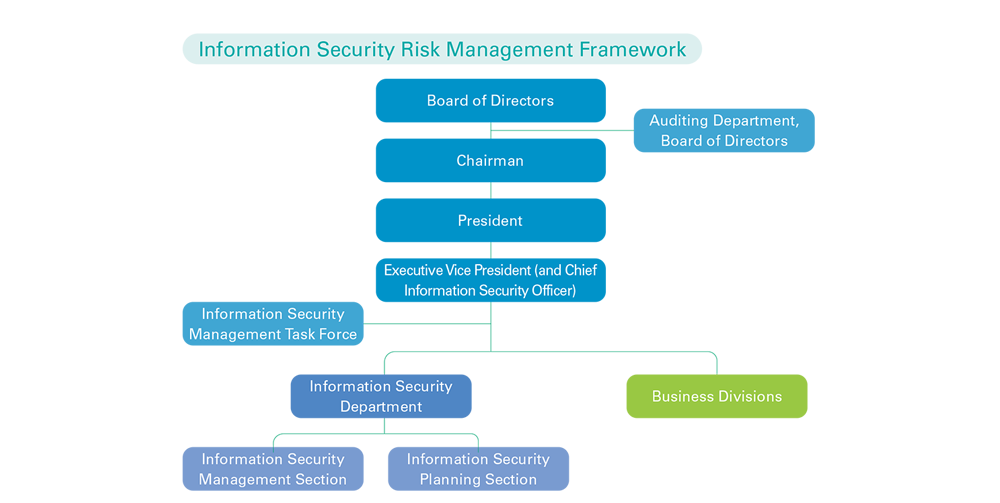
Information Security Risk Assessment and Management
Major information security incidents aimed to attack financial institutions around the world in 2021 can be divided into DDoS attacks, ATM hacks, randomware attacks, online phishing, financial institution supply chain hacks, fake financial institution apps, social engineering attacks, malware attacks and other known or potential risks. The frequency of these attacks has been rising every year, and most of the sources are international hacker organizations.
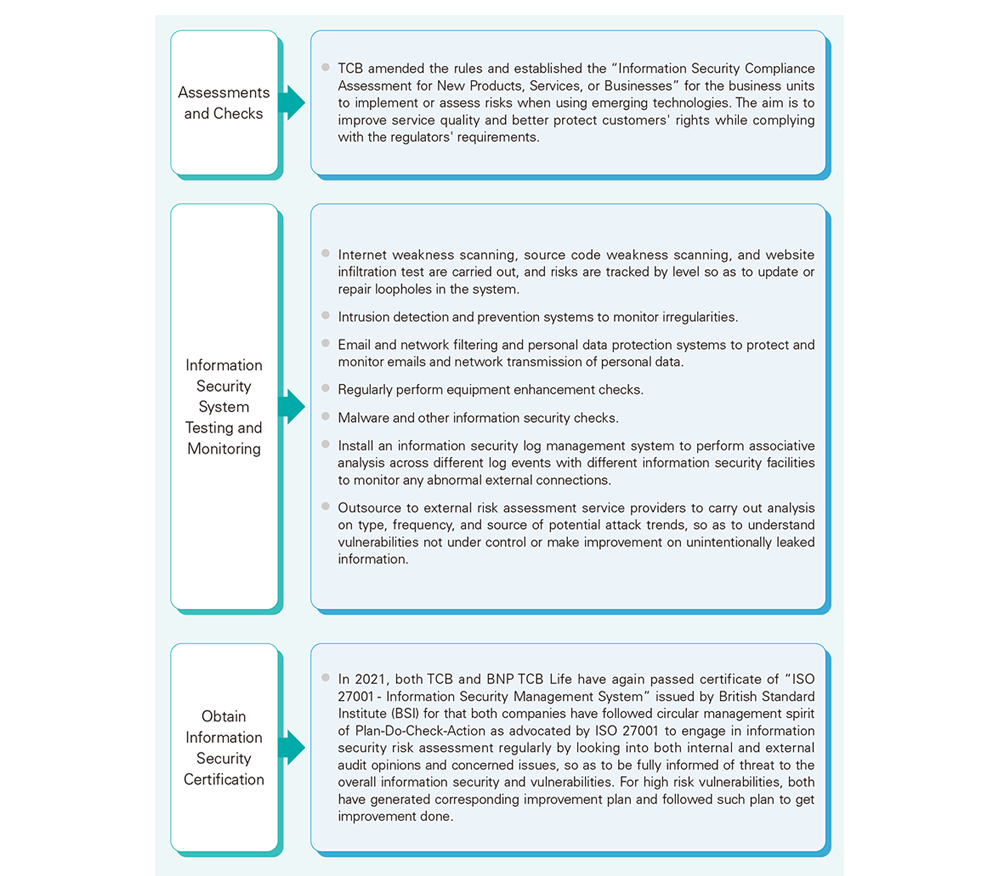
Regarding information security risks caused by emerging technologies, TCFHC's subsidiaries implement assessments and checks, perform information security system testing, and obtain information security certification as means to enforce information security management.
Regarding information security risks caused by emerging technologies, TCFHC's subsidiaries implement assessments and checks, perform information security system testing, and obtain information security certification as means to enforce information security management.
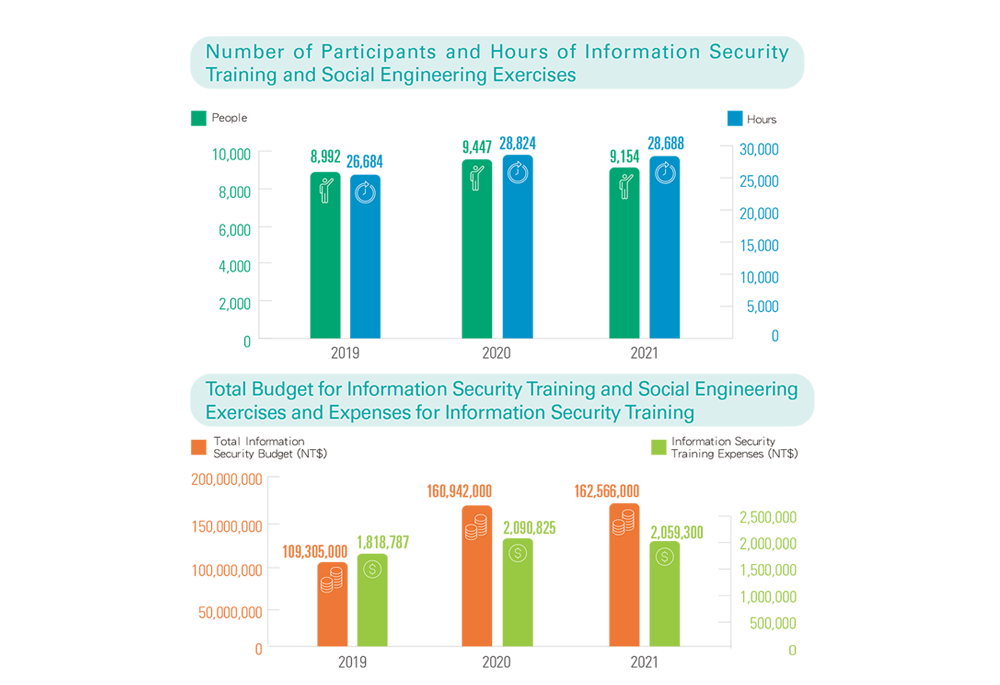
Information Security Training and Social Engineering Exercises
In order to make employees more aware of information security and more able to safeguard information, TCFHC continues to organize group-wide information security trainings every year. The completion rate for employees is 100% in 2021. In addition, both “social engineering email attack drills” and “DDoS attack drills” were held to strengthen the ability to respond to email and network attacks. The open rate and the click-to-open rates for links and attachments in the “social engineering email attack drills” had to be under 3%. All the rates were under 3% for the Group in 2021.
Personal Data Protection Policy and Organizational Structure
Given all financial services provided by the subsidiaries contain a large amount of personal data, for complete personal data protection, TCFHC has the “Personal Information File Security Maintenance Guidelines” and the “Personal Information File Security Audit Mechanisms” in place. In addition, all subsidiaries are equipped with personal data protection management policies or utilization guidelines to govern customer information collection, storage, protection, classification, and utilization. Full disclosures or notifications are provided in the products or services. In addition, guidelines are put in place for changing related information, cancelling utilization, and filing grievances.
The subsidiaries are also equipped with organizations that manage personal data protection. These organizations promote and handle security audits for personal data files as well as risk assessments and self assessments for personal data files. The subsidiaries have internal and external audits performed according to their businesses every year in order to stay updated on their personal data protection practices and make improvements.
The subsidiaries are also equipped with organizations that manage personal data protection. These organizations promote and handle security audits for personal data files as well as risk assessments and self assessments for personal data files. The subsidiaries have internal and external audits performed according to their businesses every year in order to stay updated on their personal data protection practices and make improvements.

Personal Information Training and Certification
The TCFHC Group regularly organizes personal information protection training. For instance, TCB provided the “personal information incident prevention and emergency response courses”, and BNP TCB Life rolled out “personal information protection courses” on its digital learning platform for raising security and legal awareness on the use of personal information in daily operations. In 2021, the ratio of employee receiving full course of training on personal information protection across the TCFHC Group was 100%.
In 20121, TCB and BNP TCB Life passed the “BS 10012: 2017 Personal Information Management System” certification, and TCS also passed the update verification by Taiwan Personal Information Protection & Administration System (TPIPAS).
In 20121, TCB and BNP TCB Life passed the “BS 10012: 2017 Personal Information Management System” certification, and TCS also passed the update verification by Taiwan Personal Information Protection & Administration System (TPIPAS).
Operation Procedure for Personal Information Security Event
Regarding personal information intrusion incidents, the Group has also implemented personal data incident response and reporting procedures. For example, TCB follows the “Guidelines for Handling and Reporting Personal Information Security Incidents” in handling personal information incidents involving information leaks. For general personal information incidents, the units in charge should be notified first, and the response procedure will include investigating the cause, notifying the parties involved, and discussing corrective and preventive measures. Where it involves customer information and is classified as material event, the Crisis Management Task Force will be assembled to perform post-incident response measures while staying in close communication with the customer, and issue a standard news release if necessary. Furthermore, TCB has the “Employee Rewards and Discipline Guideline” in place. Any employee found leaking business secrets or violating internal regulations will receive matching punishments. In 2021, TCFHC Group encountered no data leakage incidentsNote, no percentage of data leakage incidents related to personal information and no number of customers affected or violation of personal influence protection.
Note: The scope of data leakage events as defined by TCFHC covers only leakage of personal information of customers that occur when employees use the Internet or email to transmit such personal information.


